Transcloud
August 15, 2025

August 15, 2025
In 2025, multi-cloud isn’t a bonus—it’s the baseline.
89% of enterprises now run workloads across two or more public clouds (Flexera 2024). Why? Flexibility. Resilience. Best-in-class services from AWS, GCP, and Azure.
But managing all three in parallel? That’s where things break.
You think you’re buying optionality.
What you actually get is operational fragmentation.
Every cloud you add doesn’t just scale services—it multiplies complexity.
Suddenly, you’re running three sets of tooling, three dashboards, three policy engines.
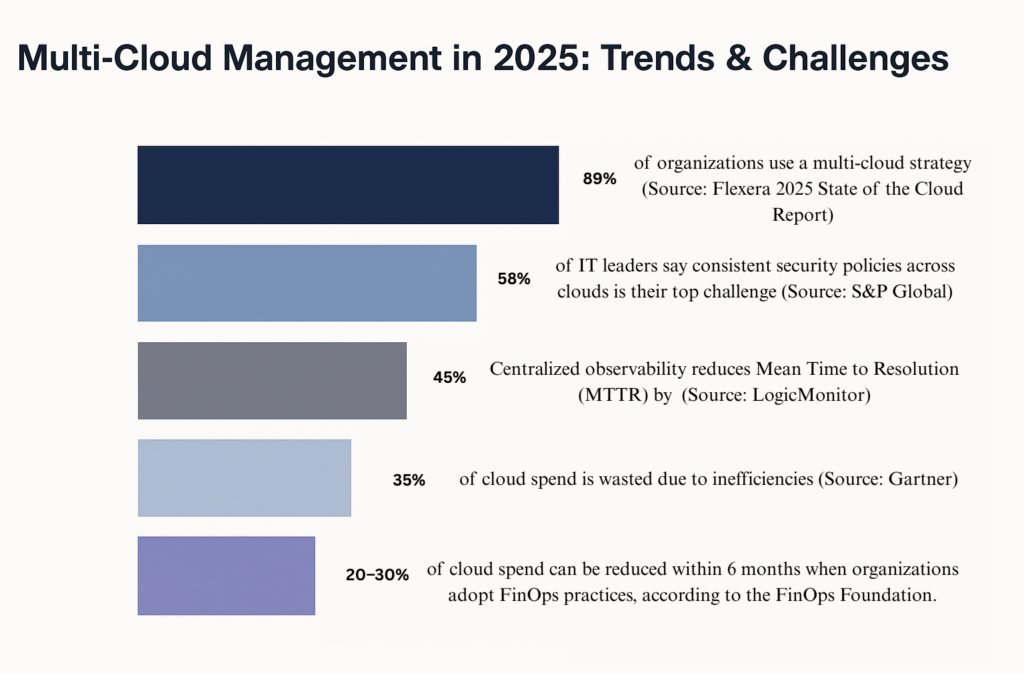
Did You Know?
Organizations using multi-cloud still struggle with visibility, automation, and integration across platforms. Here’s what 2025 looks like:
Let’s look at what that fragmentation actually does to your team:
You’re not running a cloud strategy anymore. You’re managing chaos.
Operational sprawl doesn’t just cost time—it weakens your security and your bottom line.
35% of cloud spend is wasted due to lack of cost visibility and automation (Gartner)
Cloud misconfigurations are still the #1 breach vector, according to the Cloud Security Alliance
58% of IT leaders say enforcing consistent security policies across clouds is a top challenge (sprint)
When identity, monitoring, and cost governance aren’t aligned, it’s not just a mess—it’s an attack surface. And in regulated industries like finance or healthcare? That becomes a liability.
You don’t need a magic “single pane of glass.”
What you need is platform-level abstraction—practices and tools that unify how your team builds, secures, and operates infrastructure across cloud providers.
Here’s what actually works:
Writing native infra scripts for every cloud? Unsustainable.
Modern teams standardize on Terraform, Pulumi, or Crossplane to abstract infrastructure into reusable, cloud-neutral modules.
Benefits:
A fintech client of ours reduced cloud provisioning errors by 70% after consolidating AWS and GCP infra into a shared Terraform module library
Logs and metrics don’t mean anything if you can’t correlate them.
Use tools like Datadog, Grafana Cloud, or OpenTelemetry to create a single observability pipeline across clouds.
Key capabilities:
LogicMonitor reports up to 45% lower MTTR when observability is unified across clouds.
Three cloud IAM systems = three chances to over-provision access.
Solve this with SSO, Workload Identity Federation, and codified access policies.
Your toolkit:
AWS IAM Access Analyzer, Azure Entitlement Management, and GCP’s Policy Intelligence help uncover privilege creep across federated environments.
Multi-cloud cost sprawl is real—and it’s expensive.
Use tools like:
Don’t just optimize—govern.
FinOps Foundation found that orgs who adopt cloud cost management practices reduce waste by 20–30% in 6 months.
Each cloud has its own Kubernetes flavor (GKE, EKS, AKS). But the control plane shouldn’t feel different for each.
Here’s how platform teams simplify:
This creates a single developer experience—regardless of where the workload runs.
Manual compliance checks don’t scale across clouds. Automate everything from the start.
Adopt:
Cloud governance isn’t a checklist—it’s a pipeline.
Multi-cloud doesn’t have to be a liability.
The winning teams in 2025 are those that abstract away cloud differences, enforce governance by design, and empower teams to move fast without breaking security or budget.
This is what modern, secure, cloud-native infrastructure looks like.
It’s not about choosing the “best” cloud—it’s about building a platform strategy that spans them all.
At Transcloud, we help companies simplify their infrastructure across GCP, AWS, and Azure—without reinventing the wheel for each provider.
Get a clear picture of where fragmentation is costing you—and how to align your teams on a unified infrastructure strategy.